Install and Configure the Cloud Watch Logs Agent on a Running EC2 Linux Instance
What is Cloud Watch?
Cloud watch is a monitoring service to monitor your AWS resources,
as well as the applications that you run in AWS. So the cloud watch basically monitors performance. Performance monitoring and cloud watch can monitor things like compute. Inside the compute, it can monitor things like our
EC2 instances, Auto scaling groups, Elastic Load balances, and Route 53 health checks. Cloud watch can go through and not just monitor the EC2 instances it can monitor a whole bunch of other things as well. It can monitor storage and content delivery, our EBS volumes we can monitor how busy the volumes are we can monitor storage gateways and we can monitor cloud front using cloud watch as well.
Cloud watch Pricing
It is Free
Scenario-:
Install and Configure the CloudWatch Logs Agent on a Running EC2 Linux Instance
To do this you have to log in to your Amazone account
Before Enable the Cloudwatch we have to do a few things
We have to create a Policy
We have to create a Role
Attach the IAM role To the EC2 Instances
Creating a Policy
To Create a Policy we have to go to the IAM
In IAM from the left side, panel select Policy tab to Create a new Policy
Click Create Policy
In Policy Window Select JSON tab and add the below JASON Policy
JASON
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"logs:CreateLogGroup",
"logs:CreateLogStream",
"logs:PutLogEvents",
"logs:DescribeLogStreams"
],
"Resource": [
"*"
]
}
]
}
Click Revie Policy
In the Review policy window adds the Name and Description for the Policy.
Note -: You can use any name that you like
Create Policy
After Creating the Policy you will be able to see the Policy that you have created
Creating a Role
In IAM from the left side, panel select Role tab to Create a new Role
Click Create Role
In the Creating Role Window
Select AWS services and select EC2
Click Permissions
In the Permissions Window Select the Policy That you have created Earlier
In here Permission will be granted from the policy
Click Tag
In the Tag Window, You can give a Tag for the Role in my case I gave as
Key -: Name
Value(Optional) -: CloudWatchLogAgent
Click Review
In the Review window, you can give a Name to your Role
I gave the same name as it was in the Tag
After Creating the role you will be able to see your role
Attaching an IAM Role to a Instances
Attach the IAM role and add the Details
IAM Role Select the Role That you have Created in the Role
Install and Configure the CloudWatch Logs Agent
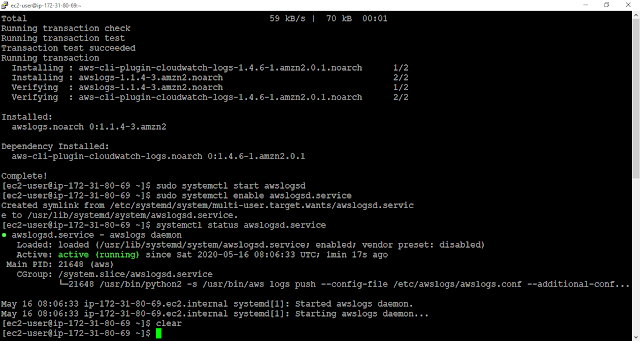
To Install the Cloud watch agent we have to log in to our Instances
Use the Putty and your Public IP to log in to your Instances
After logging to the Instances use the Below Commands to Install the Cloud Watch Agent
Fist Update your Instances
sudo yum update -y
Install the AWS Logs
sudo yum install -y awslogs
Start the AWS Log Services
sudo systemctl start awslogsd
Check the Logservicese Status (It should be active (running) )
sudo systemctl status awslogsd.service
Enable the Logservicese at each boot
sudo systemctl enable awslogsd.service
Note -: By default, the /etc/awslogs/awscli.conf points to the us-east-1 region, if you are in a different region edit the awscli.conf and add the Region that you are in. You can check your Region in top Right Conner
Check the Cloud watch Logs
To Check the Log we have to go to the Cloud Watch
Services under Management & Governance select Cloud Watch
Click Logs on the left to view the logs
Here it will show the Path that the Instance Log file is saved in
Click on the Path (/var/log/messages)
When you click on the Path you will be able to see the log file
Select the Log file and click it
This is the in datil of the Log file you can use filter events to Filter the Log
For instance, you can usee Keyword Erro to filter all errors.
Real-world Example
Using Cloud watch we can monitor the Instances log and we can have a good idea about our instance such if there are errors in that we can easily motor those using cloud watch. Moreover using these we can monitor the security issues that we are facing such as if someone has tried to hack our Server we will be able to see how many times have they tried etc..
References -:
Click hear to Visit my Facebook














No comments:
Post a Comment